Lower your guard for one second, and you’re hit by a ransomware attack which blocks access to your files and apps and extorts money from you. Prevention solutions and measures, useful tips in the event of an incident: here’s what you need to know to fight this plague.

According to Symantec, 3 million new malware appear each day, i.e. three times as many as two years ago. According to the French Ministry of Defence, 24,000 cyber-attacks were fended off in France in 2016. After FIC 2017, a forum on cyber-security which recently took place in Lille, it’s red alert this year in terms of IT security.
Ransomware is the number one IT threat. It can hit both individuals and companies’ computers and smartphones, anytime. And these programs now have a new target: connected systems.
Programs that take you hostage
How does ransomware work? Most of the time, these programs spread via email, by people inadvertently opening attachments. Opening the attachment triggers the encryption of all the files on a device, along with all the folders shared on a network. They all become inaccessible.
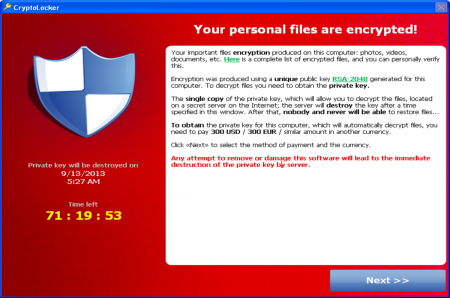
What follows is a ransom demand, as shown above, which pops up on the infected computer, with payment instructions following shortly. If you don’t pay, the threat is clear: your file will be deleted. If you do pay, a sum of money which can be rather substantial depending on the organisation under attack, you will receive an encryption key and your files will be decrypted – which, let’s be honest, is never guaranteed.
Hotels, hospitals, schools, IoT: they can all be hit.
There are more and more cases of digital extortion, hitting all sectors: tourism, healthcare, education. Very recently, an luxury Austrian hotel was hit by one of these attacks. Customers could no longer use their key cards to enter their rooms; staff couldn’t access the booking system, and the hotel paid €1,500 worth of Bitcoin to bring the situation back to normal. Many similar incidents happened in 2016.
As for the healthcare sector, the appointment system of one of UK’s largest hospital centres was paralysed for 4 days. In the USA, the Hollywood Presbyterian Medical Center had to pay $17,000 to get its IT system back. In the education sector, a college in Los Angeles paid $28,000 to regain access to its computers.
As for the Internet of Things, we also talk about Ransomware of Things (RoT). Hackers no longer block access to digital files, but to connected objects and their features, as was the case for the Austrian hotel. According to Digital Security, an Econocom Group company, the threat is expected to grow in 2017.
Whatever you do, don’t pay!
This is a worrying trend. To get back to normal, an estimated 25% to 70% of organisations are willing to pay a ransom, according to surveys, sometimes up to 1 million dollars to recover quickly from this attack. $325m was extorted in 2015, but according to Trend Micro, only 32% of the companies who pay recover their data. So paying is clearly a bad idea: it encourages hacking, as the author of a Cloud Security Alliance report on this issue believes.
How to react?
As a precautionary measure, as a user, several actions can limit risks:
- Do not open suspicious email or attachments
- Back up your files regularly
- Keep your OS, software and security apps up to date.
For companies, staff awareness is critical, because they’re the easiest way in for hackers. To limit the risks, there are solutions that improve overall IT security and allow you to analyse the behaviour of users and assets.

In of the event of an attack, switch off everything!
It’s the first measure advised by the ANSSI (National Cybersecurity Agency of France)
- Disconnect the device from the internet network. Unplug the Ethernet cable and disable the WiFi to prevent the program from spreading.
- Don’t pay the ransom: the attack can also hit your payment card. To get your files back, restore them via back-ups on another device. There are companies who specialised in file recovery.
- File a police report
For companies, getting decryption tools that are offered by IT security players and doing offline back-ups are the first measures to take. Reporting the attack and getting help from the relevant authority can limit the damage.















