Machine learning, a field of artificial intelligence, is used to automatically analyse the way interconnected systems work in order to detect cyberattacks and limit their damage. This is good news for cybersecurity players, companies, institutions and end users, who are increasingly under the threat of hacking.

Mobile devices, e-health, home automation, transport, industrial systems, smart grids, smart city: we’re living in a hyper-connected environment. The downside of the proliferation of devices and sensors, or the smartification of our world, as TechTarget calls it, is the rise of cyberattacks, some of which, such as the Mirail botnet in 2016, have devastating effects. Such DDoS attacks can cause losses in revenue of up to $205,000 an hour, according to losses in revenue of up to 250,000 dollars an hour according to ZDnet. And it could get worse.
“By 2025, over 25% of cyberattacks will be on connected devices,” according to the report on IoT security by Digital Security (Econocom Group).
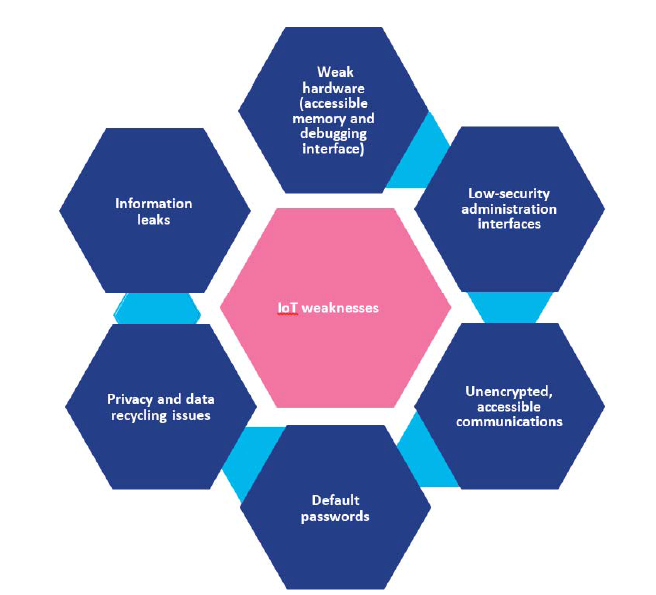
Given the increase and diversity of threats and the complex business of providing security for smart objects (see Digital Security’s graph below), artificial intelligence seems the obvious solution – combined, of course, with human supervision.
“IoT security is still in its early stages”
Efforts have been made in recent years to raise awareness among IoT players of security guidelines, such as those issued by GSMA or the ENISA in Europe. Security by design is fundamental for this, and for the whole IoT chain: designers and manufacturers of devices, component makers, software vendors, solution integrators, data processing companies, telecom carriers and security experts:
“IoT security is still in its early stages […] A number of IoT players didn’t anticipate the risk scenarios that threaten connected solutions,” says Florent Poulain, an expert at Digital Security.
Setting up a lab to assess, detect and label IoT security vulnerabilities, such as the one in Digital Security’s CERT-UBIK, is one way to address the issue of IoT security. But in a booming market, made up of a multitude of players of all sizes, such measures are fairly uncommon. But what about the devices and systems already in use?
Increasing awareness among end users about how to protect their devices (passwords, privacy settings, software updates, Wi-Fi, etc.) is also vital, although hardly a guarantee, due to the inherent vulnerabilities of connected devices, non-changeable default passwords, and the fact that manufacturers don’t issue software updates. On top of this, the very nature of the Internet of Things means that the end user of one device can’t control everything.
User and Entity Behavior Analytics (UEBA): how AI can benefit IoT
While they can’t guarantee the reliability of connected devices and solutions, experts all recommend automated monitoring of the activity on connected devices, their use and the traffic they generate on the networks and servers. Only artificial intelligence and its algorithms and datasets can do this: fast detection of attacks and limiting their spread thanks to machine learning and deep learning may still be just emerging techniques but they will be “cornerstones of tomorrow’s cyber defense”, according to Steve Grobman, Chief Technology Officer for McAfee.
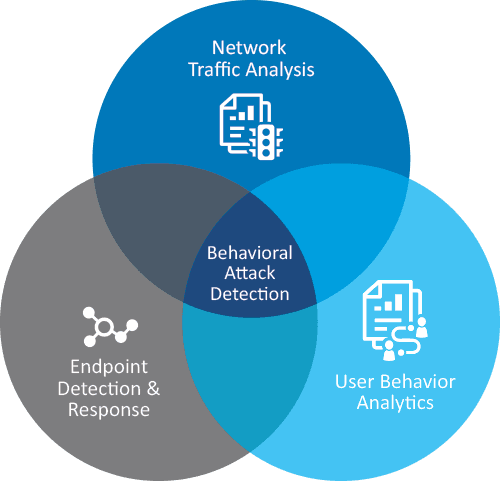 User and Entity Behavior Analytics (UEBA), which are what SIEM (Security Information and Event Management) solutions are based on, are another major IT investment trend.
User and Entity Behavior Analytics (UEBA), which are what SIEM (Security Information and Event Management) solutions are based on, are another major IT investment trend.
This technique uses machine learning capabilities to analyse behaviour logs and network traffic in real time and consequently respond in the event of an attack by getting the user to log in again, blocking an attack or assessing risk levels and alerting the company’s cybersecurity manager so they can take the necessary action.
The benefits of such solutions were highlighted at the International Cybersecurity Forum, which this year focused on hyper-connection security.
Sources : TechTarget, ZDnet, Digital Security, ENISA, Global Security Mag
Internet of Things Security, by Digital Security (Econocom Group)
Presentation of IoT ecosystems, the latest security trends, cyber-attack scenarios, recommendations, certification: this publication offers a number of expert insights into IoT security. Download it here for free.















